In an environment where "no-logs" has become a baseline marketing promise, SafePaper’s 2025 audit examines whether ten major VPN providers — both free and paid — actually uphold privacy under legal scrutiny. The report evaluates each service across jurisdiction, audit history, infrastructure design, transparency reporting, and privacy policy specificity to determine real-world no-logs compliance.
Read the full audit and VPN-by-VPN breakdown on SafePaper: "Decipher 10 No-Logs VPNs Policies & Practices (Free & Paid)"
What “No-Logs” Really Means in 2025
For something so widely claimed, “no-logs” remains widely misunderstood. At its core, the term suggests that a VPN provider does not record or store any data that could identify what a user did online, or when, or from where. But in reality, not all logs are equal — and not all “no-logs” claims mean the same thing.
VPNs inevitably collect some information to operate. This might include aggregate server load, bandwidth usage, or crash diagnostics. These are functional, non-identifiable metrics. The concern arises when providers store real IP addresses or DNS querie. Those are identifiers — and they’re exactly what a true no-logs VPN must avoid retaining.
In today’s climate of subpoenas, data-sharing alliances, and court-mandated compliance, understanding what “no-logs” actually entails is the first step. The second is knowing how to verify it — something the next section breaks down in five testable criteria.
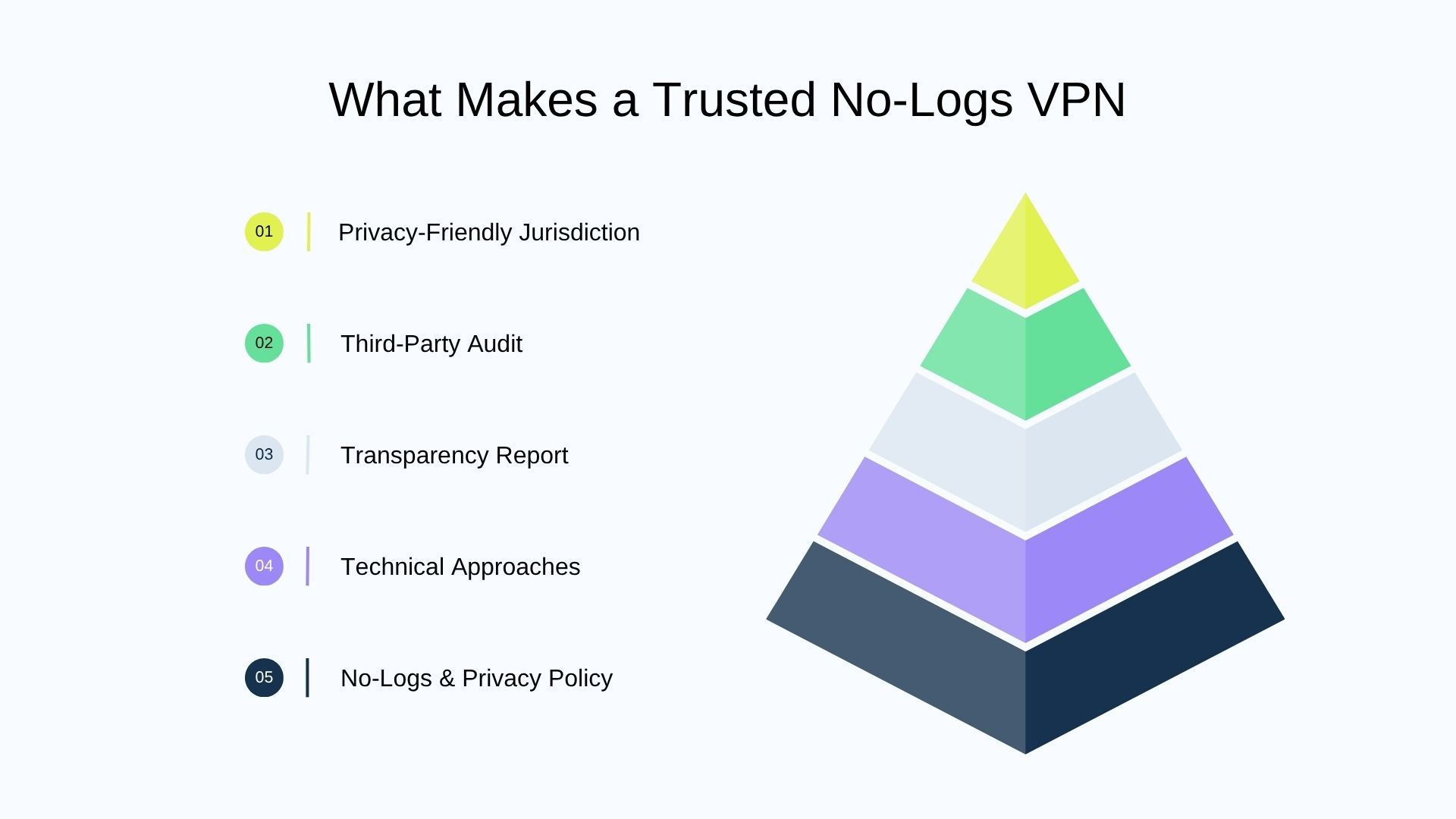
The Five Criteria for Verifying a No-Logs VPN
Marketing slogans are easy to write. Verifiable privacy is not. To move beyond blanket claims, SafePaper’s 2025 audit evaluates each VPN against five independent dimensions. Together, they form a framework that any user can use to assess whether a provider’s “no-logs” promise is structurally sound — or built on ambiguity.
1. Jurisdiction: The legal layer that overrides everything
Where a VPN is incorporated matters as much as how it’s built. Countries that are part of intelligence-sharing agreements — such as the Five Eyes (U.S., U.K., Canada, Australia, New Zealand) — may compel providers to collect and disclose user data, often under gag orders. By contrast, countries like Panama, Switzerland, and Singapore offer legal environments that make user data requests less likely and easier to resist.
A VPN headquartered in a high-risk jurisdiction cannot guarantee user privacy, regardless of its infrastructure. In several cases, SafePaper notes, providers located in the U.S. or EU have complied with subpoenas despite advertising no-logs policies.
2. Infrastructure: RAM-only servers and private DNS
Legal resilience is one half of the equation; infrastructure is the other. RAM-only servers — those that store all data in volatile memory — are wiped clean with every reboot. This minimizes the chance that session data lingers or can be forensically recovered. Similarly, running private DNS resolvers prevents DNS queries from leaking to third parties like ISPs or public DNS services.
SafePaper flags providers who still rely on disk-based servers or use third-party DNS resolvers as structurally weaker — even if their privacy policies claim otherwise.
3. Third-party audits: Proof, not promises
Independent audits conducted by firms like Deloitte, Cure53, or KPMG provide external validation of a VPN provider’s systems. These audits often examine backend logging systems, access controls, and whether servers are configured to retain any identifying data. While one audit is useful, recurring audits over multiple years show ongoing accountability.
4. Transparency reporting: A record of resistance
Transparency reports document how often providers receive data requests from authorities and whether they comply. Providers that routinely publish these reports — and maintain a record of zero user data disclosures — demonstrate both legal resolve and technical safeguards.
Conversely, the absence of a report may signal that a provider is unable or unwilling to show its record of resistance.
5. Privacy policy specificity: Clarity vs. convenience
A “we log nothing” policy may sound reassuring, but it’s often too vague to be meaningful. The most credible providers break down exactly what data they collect, why, and under what technical or legal conditions. Policies that explicitly state what is not logged — such as IP addresses, DNS queries, session metadata — offer more confidence than blanket statements or legalese.
SafePaper’s audit highlights that overly generic or overly absolute privacy policies often mask exceptions — and that fine print matters.
Paid VPNs: More Expensive, Not Always More Secure
When it comes to premium VPNs, many users assume that paying for a service guarantees superior privacy. However, SafePaper’s 2025 audit uncovers a nuanced truth: while some premium providers have impressive technical measures, their legal vulnerabilities — especially in certain jurisdictions — can compromise their no-logs claims.
If you're hesitant to commit to a long-term subscription but still want strong privacy protection, consider monthly VPN plans that offer flexibility without compromising on security.
NordVPN, ExpressVPN: Strong Privacy, Stronger Jurisdiction
Premium VPNs like NordVPN, and ExpressVPN generally receive high marks for their privacy infrastructure. Both of them have implemented cutting-edge technologies like RAM-only servers and private DNS systems, which drastically reduce the risk of data retention.
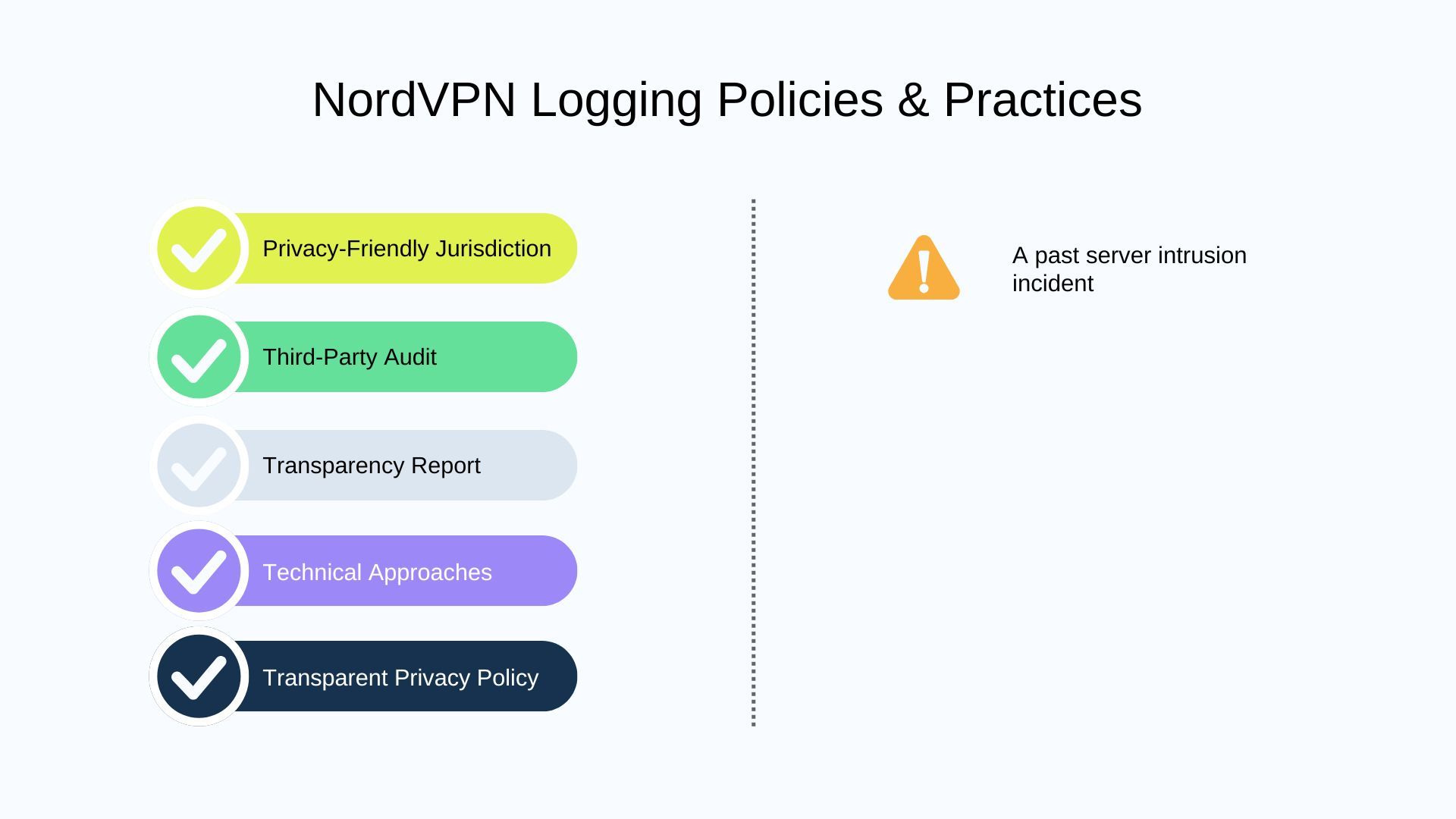
NordVPN
Based in Panama, which has no mandatory data retention laws and is not part of the Five Eyes alliance. This provides a safer legal framework, making NordVPN one of the most secure options in SafePaper’s audit.
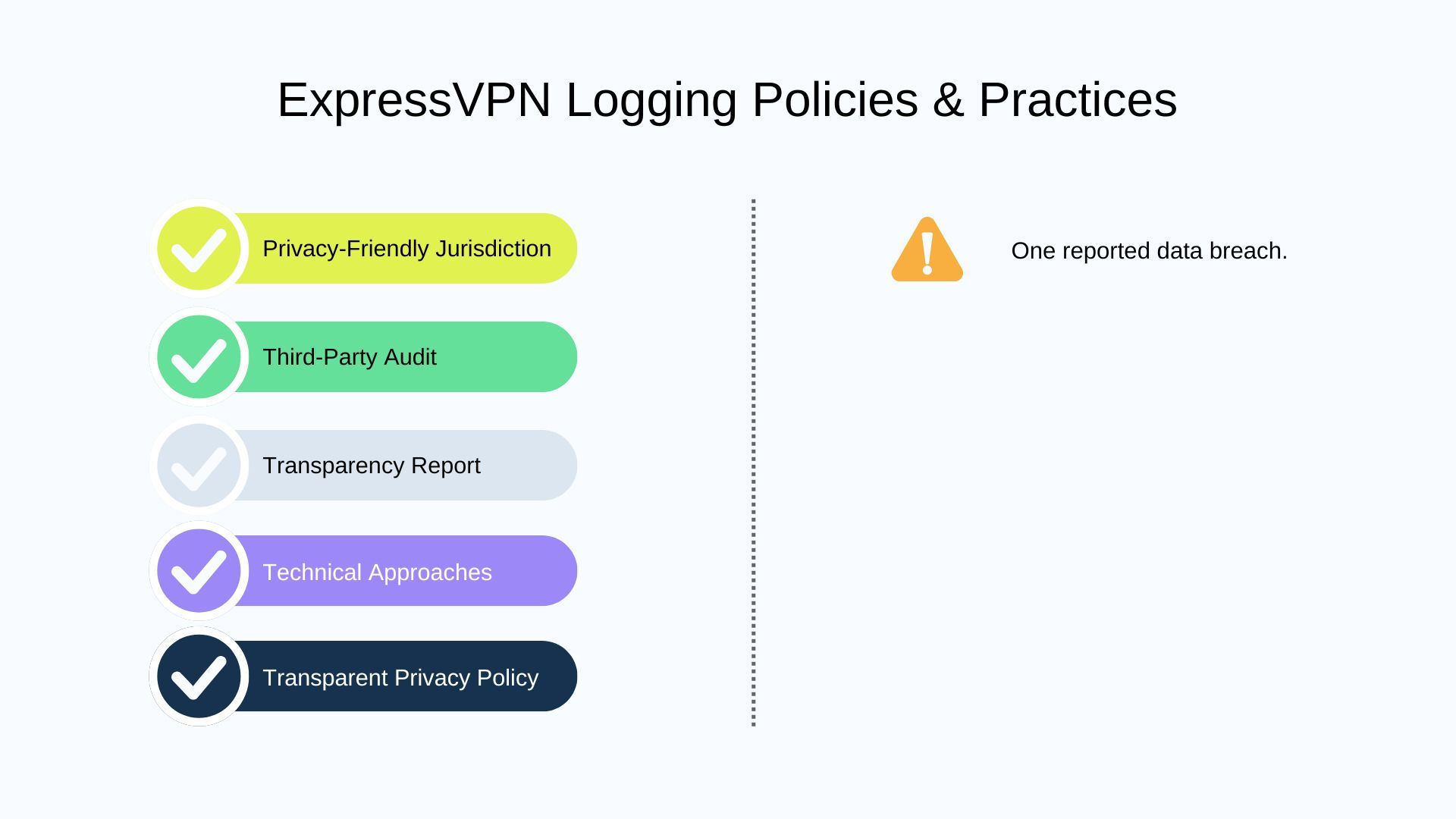
ExpressVPN
Based in the British Virgin Islands, also benefits from a strong privacy jurisdiction. Both providers regularly update their transparency reports and undergo frequent third-party audits, confirming their commitment to a no-logs policy.
Mullvad, Norton and IPVanish: Legal Exposure Overrides Technology
While all three VPNs: Mullvad, Norton, and IPVanish — boast strong technical features, they share a common vulnerability: their location in jurisdictions with high data retention obligations.
Mullvad
Despite being one of the most privacy-conscious providers with RAM-only servers and a clear no-logs policy, is based in Sweden, a member of the 14 Eyes intelligence-sharing alliance. This poses a potential risk because Swedish authorities could, in theory, demand data from Mullvad under the alliance’s surveillance agreements. In 2023, Mullvad’s infrastructure was put to the test during a police raid, and it was confirmed that no user data was found. While this proves the effectiveness of its no-logs systems, Sweden's jurisdiction remains a risk for privacy-focused users.
Norton and IPVanish
Both headquartered in the U.S. (a member of the Five Eyes), face a more immediate risk. The U.S. government can legally compel these providers to collect and hand over user data. Norton, though it employs RAM-only servers, still operates under U.S. jurisdiction, which inherently introduces a level of exposure. Similarly, IPVanish faced a significant breach of trust in 2016, when it was revealed that the VPN provider had provided connection logs to the U.S. Department of Homeland Security during a criminal investigation. While IPVanish has since implemented RAM-only servers and continues to improve its security, this past incident remains a critical cautionary tale.
Free VPNs: When Legal Foundations Beat Marketing
The general belief is that "free" VPNs come with hidden risks, often tied to data collection or selling user information. While some free providers rely on advertising revenue or data sales to sustain their service, SafePaper’s 2025 audit finds that reliable free VPNs can still offer robust privacy protection — when backed by a solid legal foundation and strong technical implementation.
ProtonVPN, Hide.me, and X-VPN: Strong Legal Foundations, Effective Tech
Among the free VPNs analyzed, ProtonVPN, Hide.me, and X-VPN stand out as exceptions to the general rule. These services may not charge a fee, but their privacy practices are built on rock-solid legal and technical foundations.
ProtonVPN
Based in Switzerland, a country known for its strong privacy laws, operates without mandatory data retention requirements. SafePaper’s audit confirms that ProtonVPN adheres to a strict no-logs policy, while also undergoing annual third-party audits for transparency. Despite not using RAM-only servers, ProtonVPN’s fully encrypted disk storage offers an alternative safeguard, ensuring that no logs are retained after use.
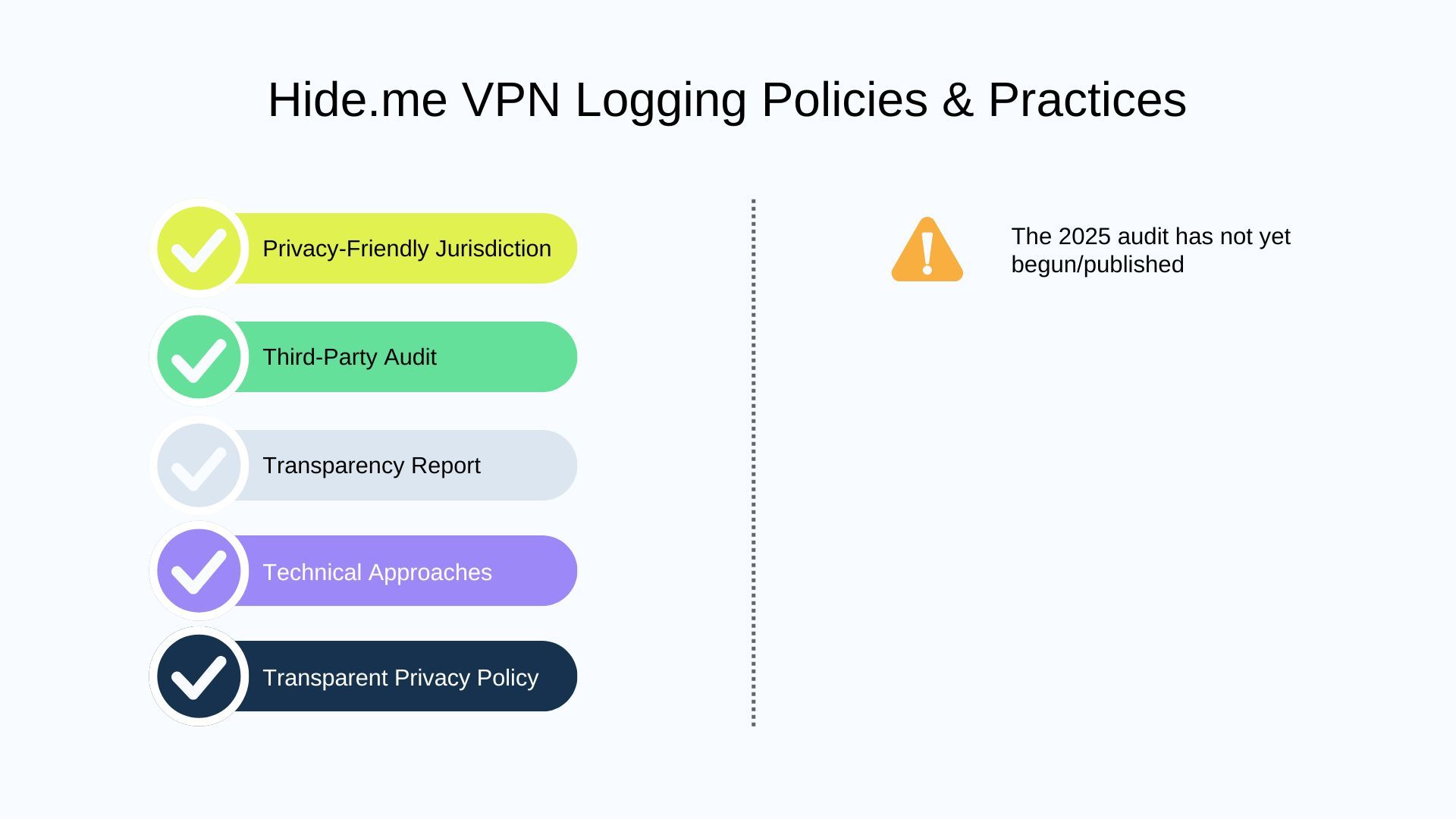
Hide.me
Based in Malaysia, another non-member of intelligence-sharing alliances, employs RAM-only servers across its entire network. With a track record of publishing transparency reports since 2013, Hide.me has demonstrated its commitment to no-logs privacy. While Malaysia’s privacy laws are less well-known compared to Switzerland’s, the lack of data retention requirements gives Hide.me a stronger legal standing than many other free providers.
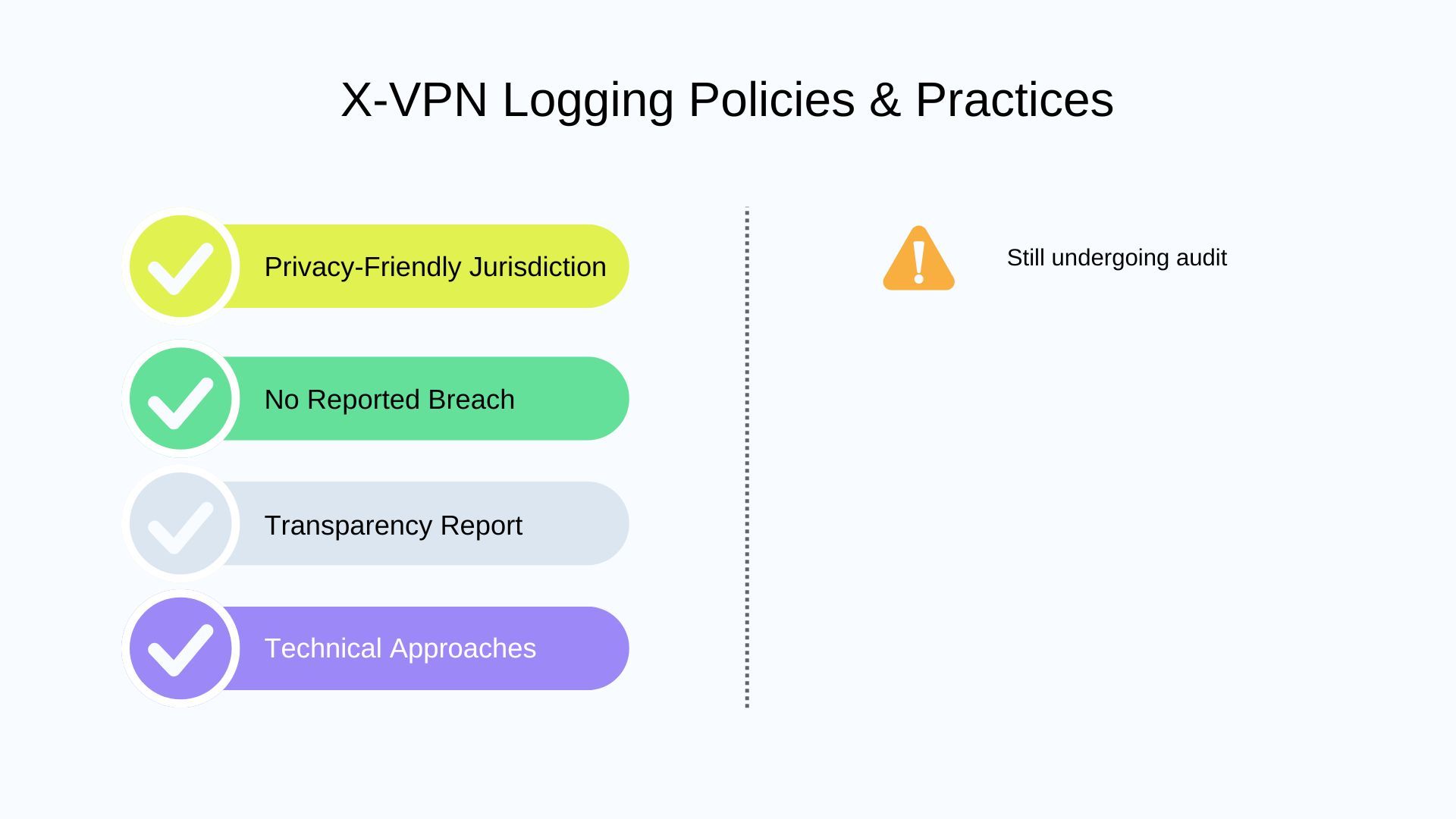
X-VPN
Headquartered in Singapore, also benefits from a favorable legal environment, operating outside the reach of Five Eyes or similar alliances. X-VPN uses RAM-only servers and private DNS, offering the same technical protections as its paid counterparts. It also maintains a history of transparency reports dating back to 2017, proving its accountability over time. Although it is still undergoing its first third-party audit, SafePaper’s review indicates that X-VPN’s commitment to privacy is credible.
TunnelBear and Windscribe: Solid Tech, Risky Jurisdictions
Not all free VPNs can claim the same level of privacy protection. TunnelBear and Windscribe, both based in Canada (a Five Eyes member), face a much higher level of legal risk despite implementing solid technical measures like private DNS servers and RAM-only architecture.
TunnelBear
Acquired by McAfee in 2018, has long been known for its strong security features. However, its Canadian headquarters places it within the Five Eyes jurisdiction, subjecting it to legal requests for data. Although it has passed several independent audits for app security, its lack of transparency regarding no-logs compliance raises concerns for users prioritizing jurisdictional safety.
Windscribe
Another free provider with strong technical capabilities, including RAM-only servers and private DNS resolvers. However, it operates out of Canada, which means it is vulnerable to legal requests from government agencies. Windscribe does regularly publish transparency reports, but its jurisdictional risk remains a concern.
Takeaways for Users: How to Vet a VPN Yourself
After reviewing 10 leading VPNs through the lens of five key criteria, SafePaper’s 2025 audit provides essential insights into what users should prioritize when selecting a VPN. Whether you’re paying for a premium service or opting for a free VPN, these three core questions can help you assess a provider’s true commitment to privacy:
1. Where is the VPN based?
Jurisdiction is the single most important factor when it comes to privacy. If a VPN is based in a country that is part of an intelligence-sharing alliance (like the Five Eyes), it is subject to laws that could force it to collect and share user data with authorities. Look for VPNs headquartered in countries with no mandatory data retention laws and those outside surveillance alliances — such as Panama, the British Virgin Islands, Singapore and Switzerland. These jurisdictions offer the best legal protections for user privacy.
2. What technical measures does the VPN implement?
The right infrastructure can make a significant difference. VPNs that use RAM-only servers ensure that no data is stored long-term, reducing the risk of logs being accessed. Private DNS servers further protect against leaks, preventing your browsing behavior from being exposed to third-party entities. Ensure the provider uses strong encryption, regular server audits, and has transparent privacy policies that are easy to understand.
3. Has the VPN been independently audited?
A third-party audit is one of the most reliable ways to verify a VPN’s no-logs claims. These audits examine the provider’s backend systems and security infrastructure to confirm that they’re following their public privacy policies. It’s a good sign if the VPN has undergone regular audits over multiple years. If a VPN hasn’t been audited, or only conducted an audit once with no follow-up, that should raise a red flag.
The Bottom Line: Don’t Settle for Promises — Demand Proof
In 2025, privacy demands proof — not promises. The VPN industry is flooded with marketing slogans and vague claims, but real privacy protection requires more than flashy ads. For users who prioritize privacy, it’s not enough to simply trust a VPN’s claim of “no-logs.” Demand the evidence, and make your choice accordingly.
About SafePaper
SafePaper is an independent digital privacy publication based in the U.S., focused on trustworthy, no-fluff guides for everyday internet users. Its team of researchers manually tests VPNs, browsers, and privacy tools to help users stay safe, stay informed, stay free. To learn more, visit safepaper.io.
Media Contact
Paige West
support@safepaper.io